Simulating and Detecting Malware Attacks on Linux With ClamAV
Mon, 29 Sep 2025 13:43:24 +0530

Linux may feel secure, but it’s not immune to malware. Servers, VPS, and even IoT devices can be targeted by malicious actors. The good news? You can detect and defend against some threats using ClamAV, an open-source antivirus engine.
Now, ClamAV is not your typical antivirus, as it may throw plenty of false positives and you need to analyze if there are actual threats.
In this guide, I’ll show you how to simulate malware attacks safely using the EICAR test file (don’t worry, it’s completely harmless!) and how to detect them on your Linux system. By the end, you’ll know how to integrate ClamAV into your workflow for continuous protection.
Step 1: Using ClamAV

ClamAV is an open-source antivirus engine designed for detecting malware, trojans, viruses, and other malicious threats on Linux and Unix systems.
Linux servers often host websites, applications, or shared directories. Even though Linux is generally secure, malware can still sneak in via uploads, compromised repos, or misconfigured services.
ClamAV helps detect malicious files before they cause damage, acting as a first line of defense in a multi-layered security strategy.
How ClamAV works:
- Signature updates: ClamAV downloads the latest malware definitions via
freshclam. - Scanning: You scan files or directories with
clamscanorclamdscan. - Detection: If a file matches a known signature, ClamAV reports it as infected.
- Optional removal: You can remove or quarantine infected files automatically.
Installing ClamAV is straightforward. On Debian-based systems, run:
sudo apt update
sudo apt install clamav clamav-daemon -y
clamav: the main scanning engineclamav-daemon: keeps ClamAV running in the background for faster scans
Start the daemon if you want it running continuously:
sudo systemctl start clamav-daemon
Step 2: Update Virus Signatures
Before scanning anything, make sure your virus definitions are up-to-date:
sudo freshclam
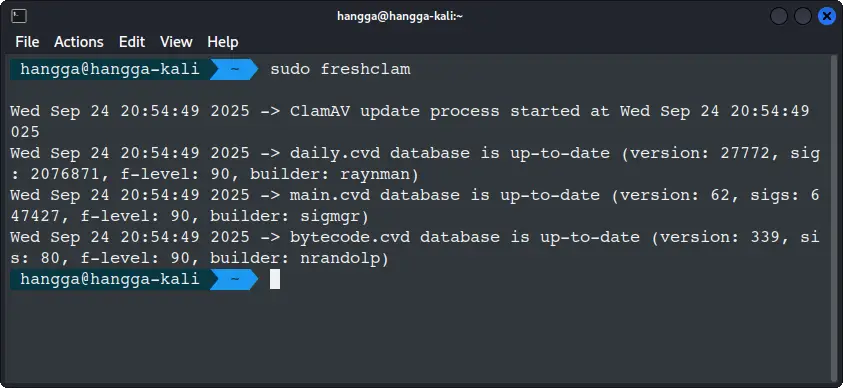
ClamAV relies on a signature database. If it’s outdated, it might miss newer malware.
Step 3: Simulate a Malware Attack
Before you test ClamAV, you need a “fake malware” file. Enter EICAR.
Think of EICAR as a “fake virus” that is completely safe. It was created specifically to test antivirus software without putting your computer at risk.
- EICAR is not a real virus. it cannot harm your files or steal your data.
- Antivirus programs, including ClamAV, will detect this file as if it were malware.
This allows you to check whether your antivirus is working correctly. A good way for demonstrating malware detection in labs or tutorials.
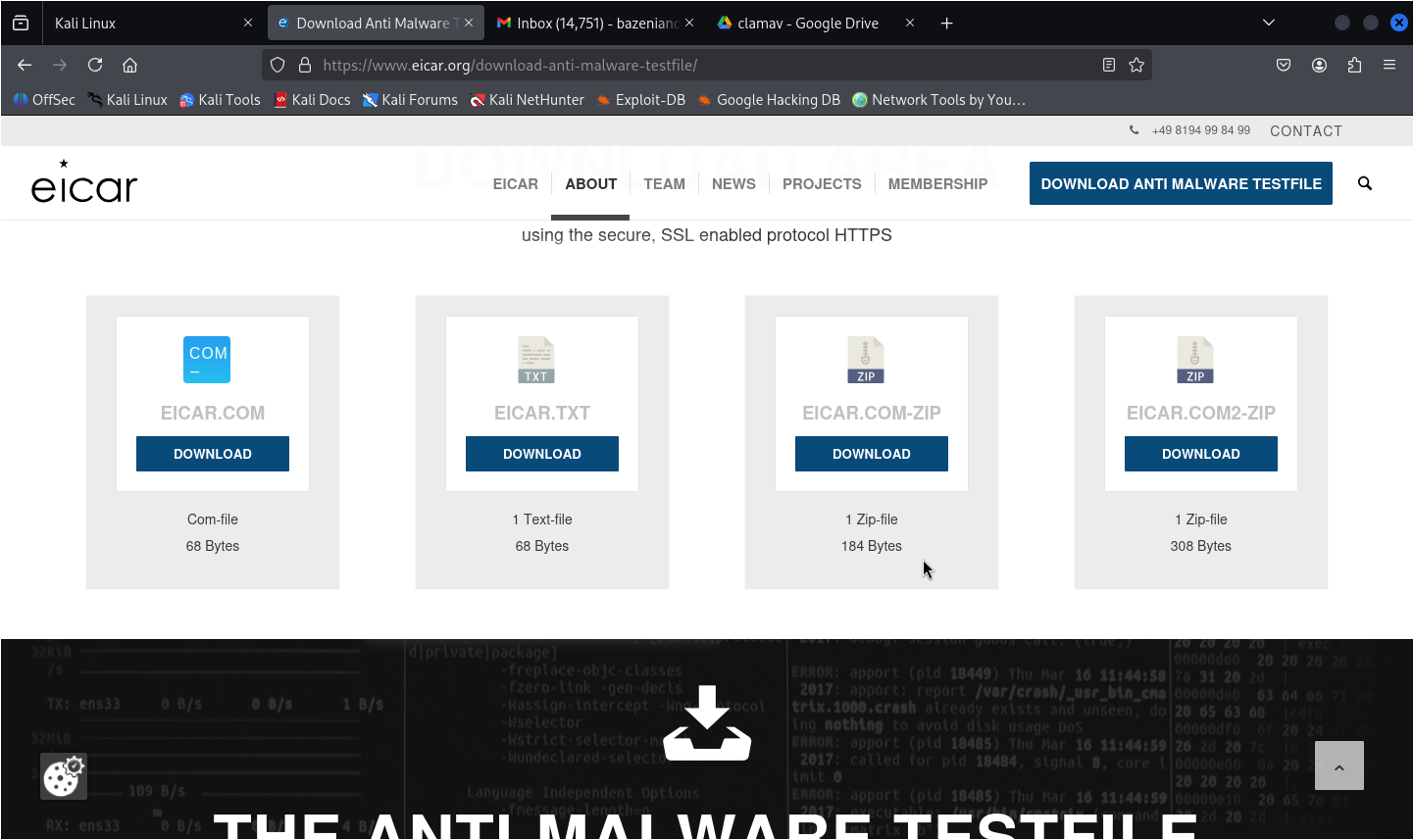
Download the EICAR test file:
curl -O https://secure.eicar.org/eicar.com.txt
There are other types of test files too:
Step 4: Scan the Test File
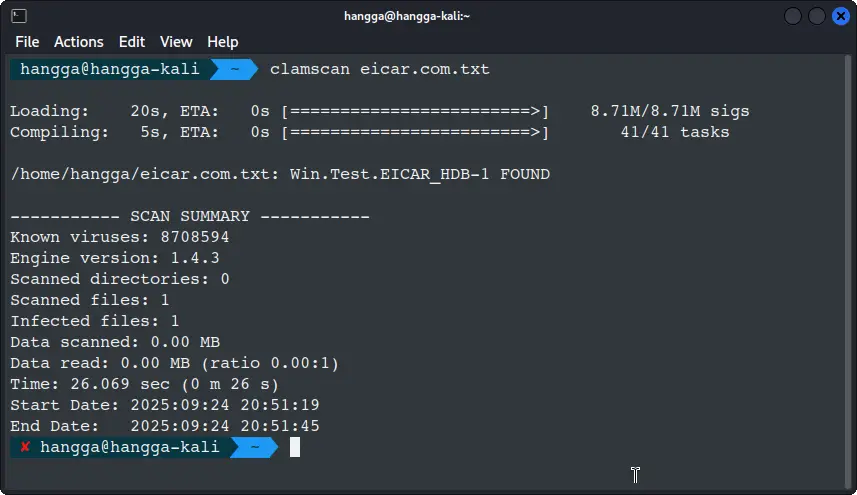
Scan the file manually:
clamscan eicar.com.txt
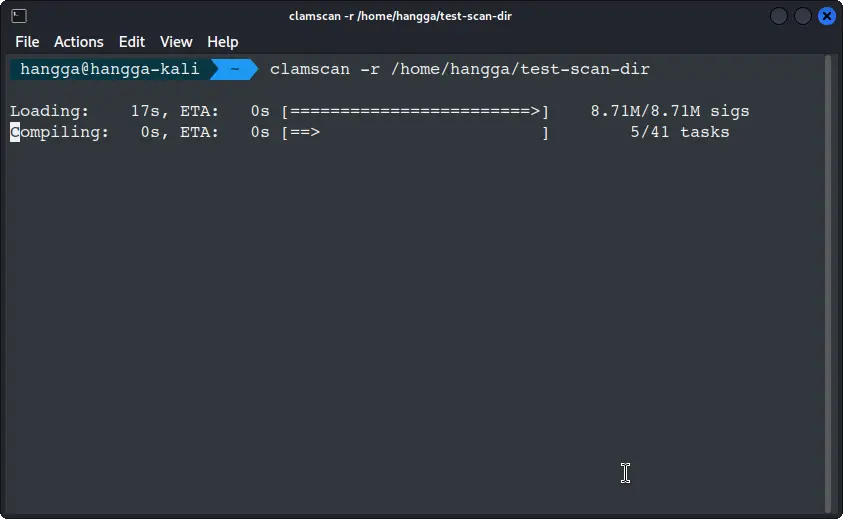
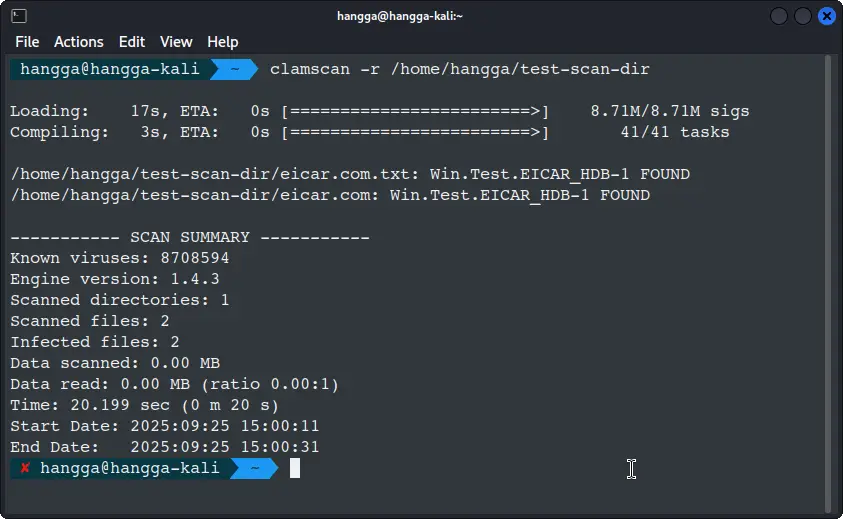
Scan the directories:
clamscan -r /<directory>
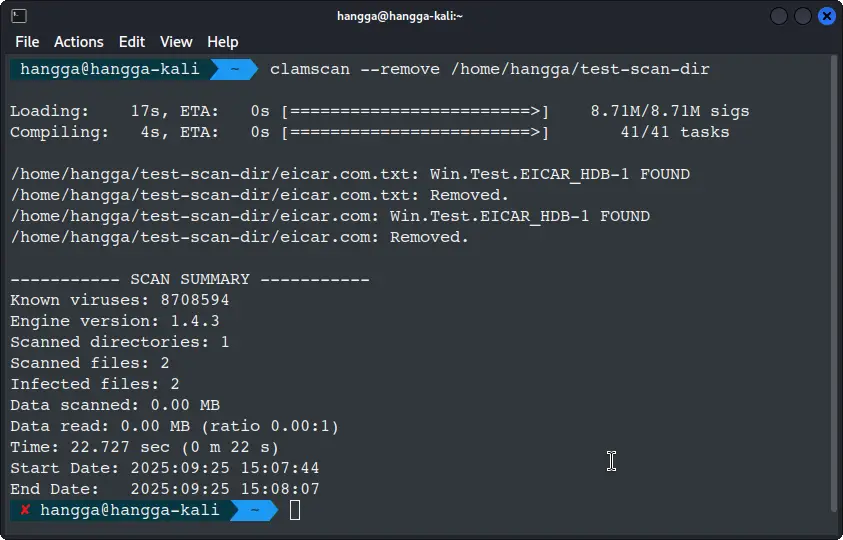
clamscan --remove /<directory>
Step 5: Automate Scans with Cron
You can use cron jobs to schedule scans to run automatically. For example, to scan /var/www every day at 3 AM and log results:
0 3 * * * clamscan -r /var/www --log=/var/log/clamav/scan.log
Conclusion
ClamAV is signature-based, meaning it works best for malware that’s already known and included in its database. It won't work with zero-day malware, fileless attacks, obfuscated/polymorphic malware. Still, it is good to have some sort of defense, especially for scanning new uploaded files and cloned repositories.
Of course, up your defenses with firewalls & log monitoring, sandbox the uploaded files and follow best practices.
Recommended Comments