How to Fingerprint Websites With WhatWeb - A Practical, Hands-On Guide
Fri, 17 Oct 2025 17:59:33 +0530

This short guide will help you get started with WhatWeb, a simple tool for fingerprinting websites. It’s written for beginners who want clear steps, short explanations, and practical tips. By the end, you’ll know how to run WhatWeb with confidence.
What is WhatWeb?
Imagine you’re curious about what powers a website: the CMS, web server, frameworks, analytics tools, or plugins behind it. WhatWeb can tell you all that right from the Linux command line. It’s like getting a quick peek under the hood of any site.
In this guide, we’ll skip the long theory and go straight to the fun part. You’ll run the commands, see the results, and learn how to understand them in real situations.
Legal and ethical note
Before you start, here’s a quick reminder. Only scan websites that you own or have clear permission to test. Running scans on random sites can break the law and go against ethical hacking practices. If you just want to practice, use safe test targets that are made for learning.
For the examples in this guide, we will use http://www.vulnweb.com/ and some of its subdomains as safe test targets. These sites are intentionally provided for learning and experimentation, so they are good places to try WhatWeb without worrying about legal or ethical issues.
Install WhatWeb
Kali Linux often includes WhatWeb. Check version with:
whatweb --version
If not present, install with:
sudo apt update
sudo apt install whatweb
Quick basic scan
Run a fast scan with this command. Replace the URL with your target.
whatweb http://testphp.vulnweb.com
This prints a one-line summary for the target. You will see status code, server, CMS, and other hints:
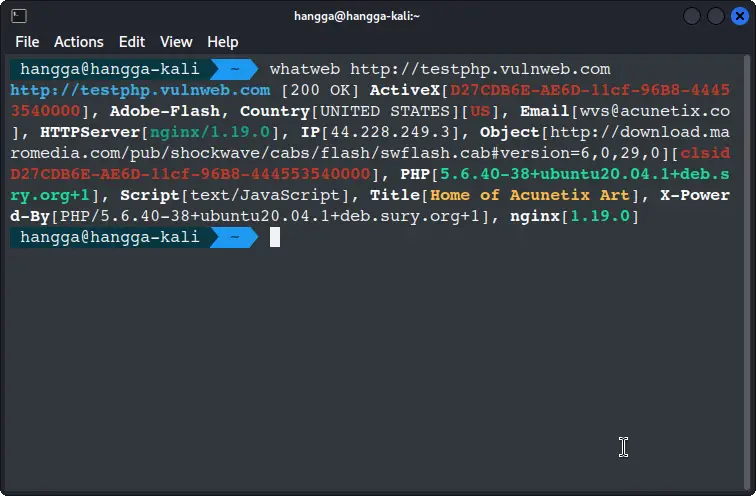
Beyond basic scan: Getting more out of whatweb
The above was just the very basic usse of whatweb. Let's see what else we can do with it.
1. Verbose output
whatweb -v http://testphp.vulnweb.com
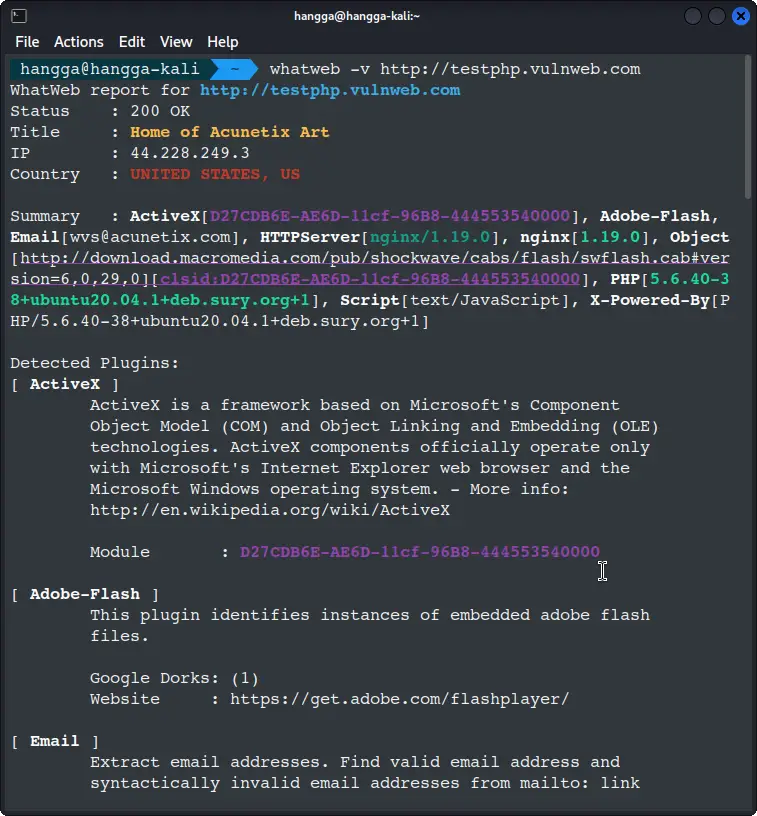
This shows more details and the patterns WhatWeb matched.
WhatWeb report for http://testphp.vulnweb.com
Status : 200 OK
Title : Home of Acunetix Art
IP : 44.228.249.3
Country : UNITED STATES, US
Summary : ActiveX[D27CDB6E-AE6D-11cf-96B8-444553540000], Adobe-Flash, Email[wvs@acunetix.com], HTTPServer[nginx/1.19.0], nginx[1.19.0], Object[http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=6,0,29,0][clsid:D27CDB6E-AE6D-11cf-96B8-444553540000], PHP[5.6.40-38+ubuntu20.04.1+deb.sury.org+1], Script[text/JavaScript], X-Powered-By[PHP/5.6.40-38+ubuntu20.04.1+deb.sury.org+1]
Detected Plugins:
[ ActiveX ]
ActiveX is a framework based on Microsoft's Component
Object Model (COM) and Object Linking and Embedding (OLE)
technologies. ActiveX components officially operate only
with Microsoft's Internet Explorer web browser and the
Microsoft Windows operating system. - More info:
http://en.wikipedia.org/wiki/ActiveX
Module : D27CDB6E-AE6D-11cf-96B8-444553540000
[ Adobe-Flash ]
This plugin identifies instances of embedded adobe flash
files.
Google Dorks: (1)
Website : https://get.adobe.com/flashplayer/
[ Email ]
Extract email addresses. Find valid email address and
syntactically invalid email addresses from mailto: link
tags. We match syntactically invalid links containing
mailto: to catch anti-spam email addresses, eg. bob at
gmail.com. This uses the simplified email regular
expression from
http://www.regular-expressions.info/email.html for valid
email address matching.
String : wvs@acunetix.com
String : wvs@acunetix.com
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : nginx/1.19.0 (from server string)
[ Object ]
HTML object tag. This can be audio, video, Flash, ActiveX,
Python, etc. More info:
http://www.w3schools.com/tags/tag_object.asp
Module : clsid:D27CDB6E-AE6D-11cf-96B8-444553540000 (from classid)
String : http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=6,0,29,0
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.6.40-38+ubuntu20.04.1+deb.sury.org+1
Google Dorks: (2)
Website : http://www.php.net/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/JavaScript
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.6.40-38+ubuntu20.04.1+deb.sury.org+1 (from x-powered-by string)
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.19.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.19.0
Date: Mon, 13 Oct 2025 07:29:42 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: close
X-Powered-By: PHP/5.6.40-38+ubuntu20.04.1+deb.sury.org+1
Content-Encoding: gzip
2. Aggressive scan (more probes)
whatweb -a 3 http://testphp.vulnweb.com
Use aggressive mode when you want more fingerprints. Aggressive mode is slower and noisier. Use it only with permission.
3. Scan a list of targets
Create a file named targets.txt with one URL per line.
nano targets.txt
When nano opens, paste the following lines exactly (copy and right-click to paste in many terminals):
http://testphp.vulnweb.com/
http://testasp.vulnweb.com/
http://testaspnet.vulnweb.com/
http://rest.vulnweb.com/
http://testhtml5.vulnweb.com/
Save and exit nano by pressing ctrl+X. Confirm the file was created for the sake of it:
cat targets.txt
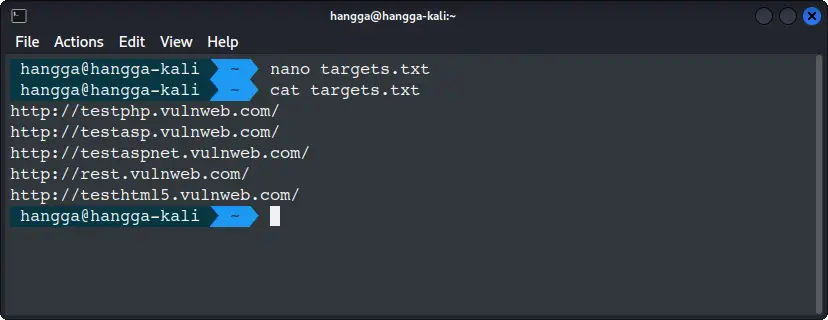
You should see the five URLs listed. Then run:
whatweb -i targets.txt --log-json results.json
This saves results in JSON format in results.json.
What to expect on screen: WhatWeb prints a per-host summary while it runs. When finished, open the JSON file to inspect it:
less results.json
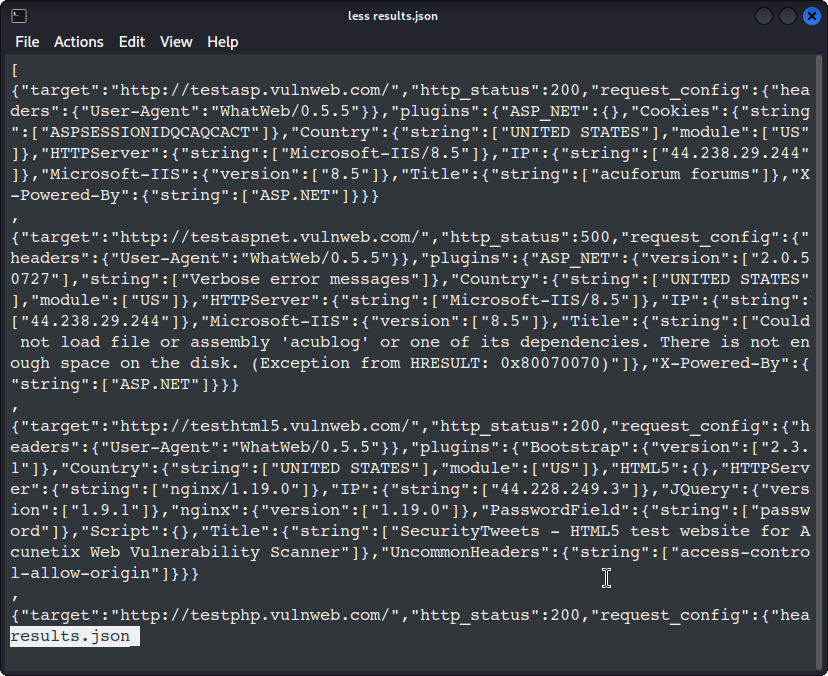
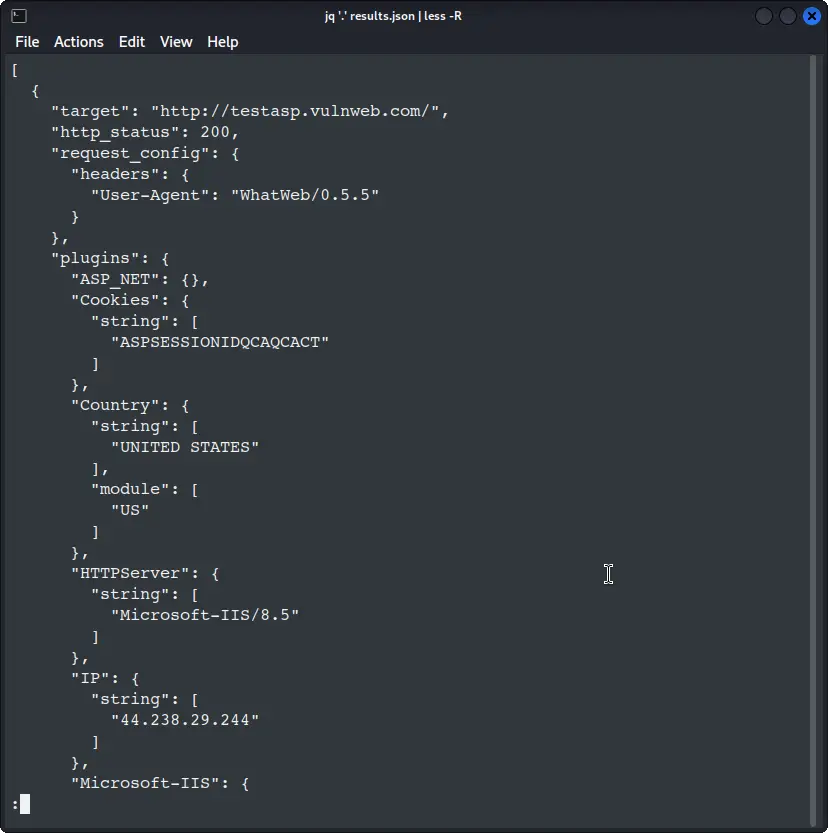
If you want a pretty view and you have jq installed, run:
jq '.' results.json | less -R
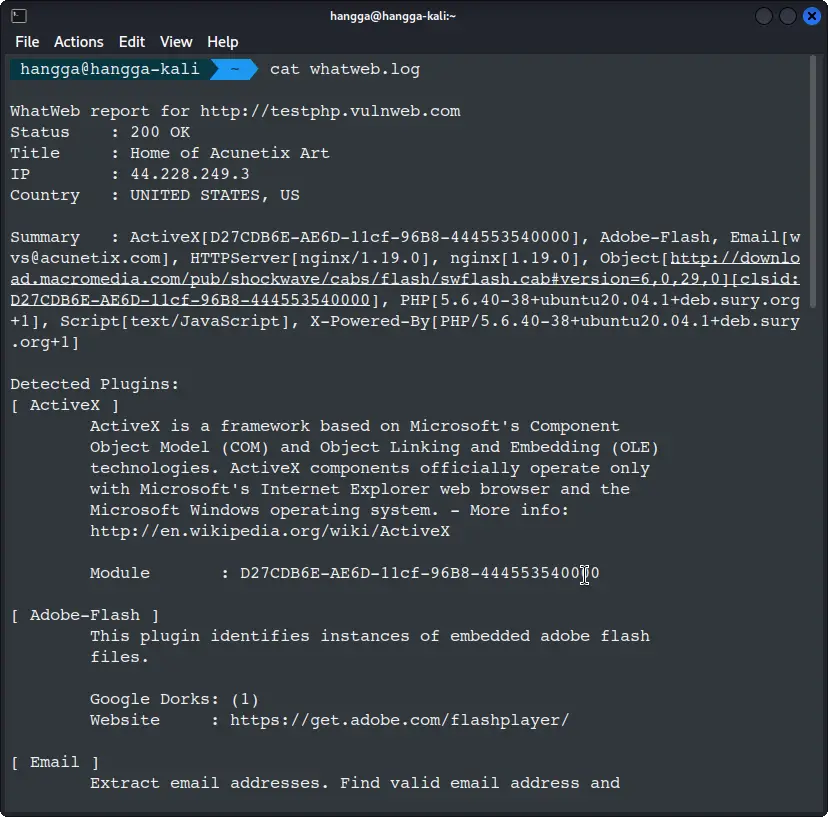
4. Save a human readable log
whatweb -v --log-verbose whatweb.log http://testphp.vulnweb.com
Let's see the log:
cat whatweb.log
5. Use a proxy (for example Burp Suite)
whatweb --proxy 127.0.0.1:8080 http://testphp.vulnweb.com
6. Custom user agent
If a site blocks you, slow down the scan or change the user agent.
whatweb --user-agent "Mozilla/5.0 (Windows NT 10.0; Win64; x64)" http://testphp.vulnweb.com
7. Limit scan to specific ports
WhatWeb accepts a URL with port, for example:
whatweb http://example.com:8080
Interpreting the output
A typical WhatWeb line looks like this:
http://testphp.vulnweb.com [200 OK] Apache[2.4.7], PHP[5.5.9], HTML5
- 200 OK - HTTP status code. It means the request succeeded.
- Apache[2.4.7] - the web server software and version.
- PHP[5.5.9] - server side language and version.
- HTML5 - content hints.
If you see a CMS such as WordPress, you may also see plugins or themes. WhatWeb reports probable matches. It is not a guarantee.
Combine WhatWeb with other tools
WhatWeb is best for reconnaissance. Use it with these tools for a fuller picture:
- nmap - for network and port scans
- dirsearch or gobuster - for directory and file discovery
- wpscan - for deeper WordPress checks
A simple workflow:
- Run WhatWeb to identify technologies.
- Use nmap to find open ports and services.
- Use dirsearch to find hidden pages or admin panels.
- If the site is WordPress, run wpscan for plugin vulnerabilities.
Conclusion
WhatWeb is a lightweight and fast tool for fingerprinting websites. It helps you quickly understand what runs a site and gives leads for deeper testing. Use the copy-paste commands here to get started, and combine WhatWeb with other tools for a full reconnaissance workflow. Happy pen-testing 😀
Recommended Comments