Tails OS Tutorial | Features, Installation, Pros, Cons
Sat, 31 May 2025 12:15:51 +0000
Tails is a Tor-based project inspired by the Debian Linux distro. Tails works on Tor Foundation, i.e., the onion router. It is supposed to be a secure OS and difficult to trace with ordinary tools/tricks.
Tails is used to perform privacy-focused tasks without leaving digital traces. These tasks include accessing or monitoring the target, i.e., it is recommended to access the identity type of data ethically (with consent of the target).
Today, this guide brings a brief walkthrough of the Tails OS and also lists the process to set up Tails.
- Tails OS | A Quick Walkthrough
Tails OS | A Quick Walkthrough
Let’s have a quick walkthrough of the features, some facts, and tools that Tails has:
Tails Development and Merger With Tor
- Tails was first released in 2009 as an iteration of Incognito, a Gentoo-based Linux distribution.
- The Tails project was originally named “Amnesia,” and now “Amnesia” is the default username/hostname of the Tails OS.
- In 2023, the Tails submitted a request to merge with Tor, which was completed in 2024, and now Tails is a Tor project.
Release Cycle
- Tails usually release the update after every 6-8 weeks. However, the major release (Like 5.0, 6.0, 7.0) is expected approximately every 2 years.
Top Features of Tails OS
- Communication via Tails is done using Tor (The Onion Router).
- Direct or non-Tor traffic is blocked by default.
- Can create persistent (keeping the data) and non-persistent (temporary) storage.
- Tails verifies and authenticates the Tails version you acquire.
- Wipes out the memory (RAM) after every reboot or shutdown, nullifying the chance of accessing the sensitive data, i.e., passwords, logins, etc, after restarts/ shutdowns.
- MAC Address Spoofing
Built-in Security and Privacy Tools for Maximum Anonymity
-
- Tor Network: An Anonymous network to route traffic anonymously.
- Thunderbird: An email client to send/receive encrypted emails.
- KeePassXc: A password manager to securely save passwords.
- Electrum: Bitcoin wallet
- OnionShare: Sharing files/media anonymously
- MAT2: A tool to remove metadata from files, i.e., PDF.
- GnuPG (GPG): Tool for encrypting, signing, and verifying emails, using Public-Key cryptography.
Persistent Vs Non-Persistent Storage in Tails
Before proceeding to its setup, let‘s have a look at the difference between Persistent and Non-Persistent.
| Feature | Persistent | Non-Persistent |
|---|---|---|
| Data Saving | Yes | No |
| Boot Time | Slight Longer | Faster than Non-persistent |
| Recommended For | When you want to have the data in the upcoming sessions. | Maximum Anonymity |
How to Install and Set up Tails on a USB Drive (Step-by-Step Guide)
Why are you installing Tails? If the purpose is anonymity, you need to create a non-persistent Live USB. However, if the purpose is to learn and implement, then you can create a persistent one to keep the history and some data from the previous sessions.
- Recommended: Use Tails as a Live OS, i.e., a non-persistent OS.
- Not Recommended: Avoid installing it on your primary host or primary virtual machine, where traces can persist.
Hardware Requirements for Installing Tails
- 64-bit processor
- Minimum 2GB RAM (Recommended is 4GB)
- Minimum 8 GB USB drive (Recommended is 16GB)
Step 1: Download and Verify the Tails OS Disk Image (For USB or Virtual Machines)
Download the Tails (either for USB sticks or the ISO file for Virtual machines).

Download Tails:
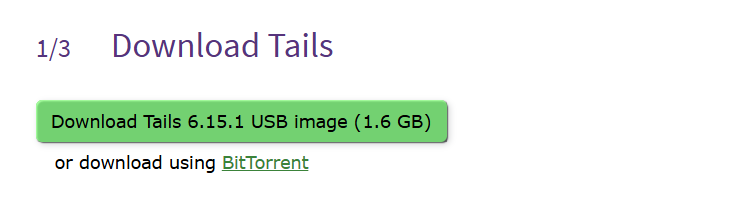
Once downloaded, verify your downloaded version:
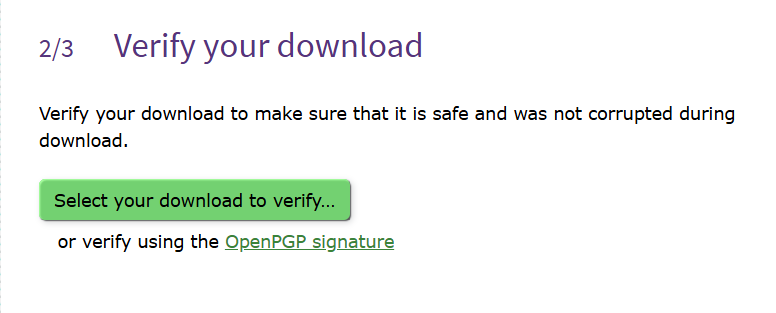
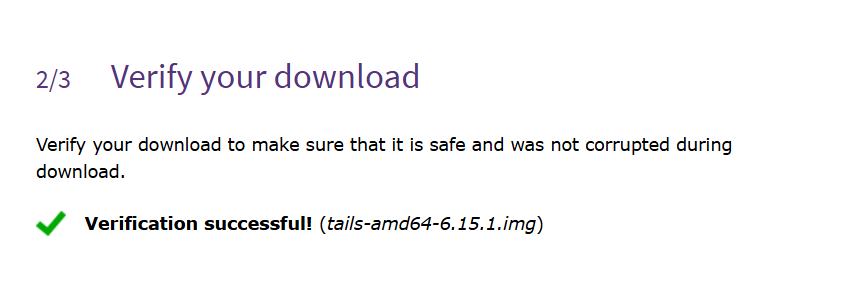
Confirm that the verification is successful before proceeding further:
Step 2: Install Tails
Once done, you must have a USB bootable tool like balenaEtcher (if using Linux), Rufus (if using Windows), etc. Here, I have listed two possibilities:
- Installation Option 1: Installing Tails Using the GNOME Disks App
- Installation Option 2: Installing Tails Using the Balena Etcher
- Installation Option 1: GNOME Disks App
If you are using a GNOME desktop environment, you can make the Tails USB using the GNOME Disks Desktop application. Here’s the process.
Attach the USB with the Linux OS, and open the “GNOME Disks” app. Now, select the USB and click the “vertical ellipsis”.
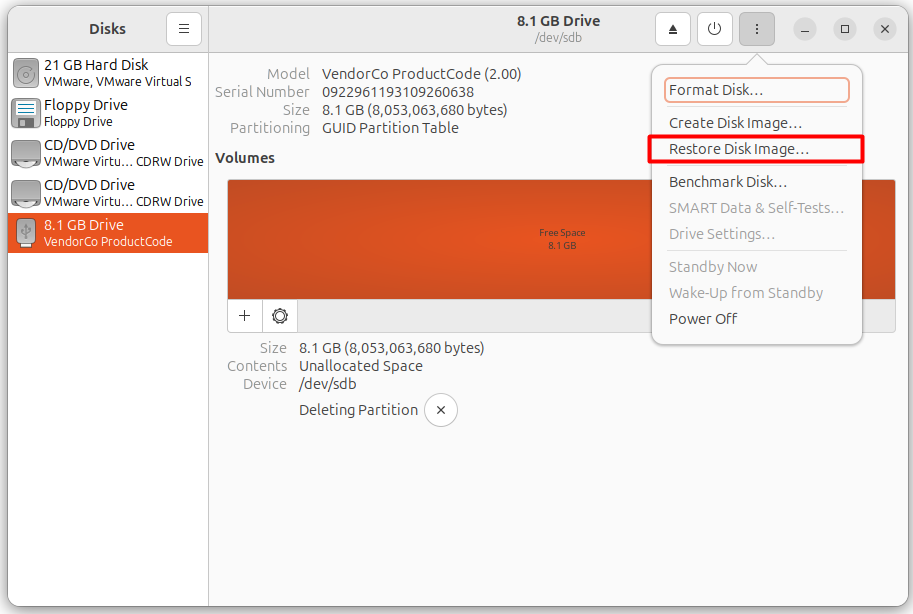
It will then ask you to choose the Disk Image:
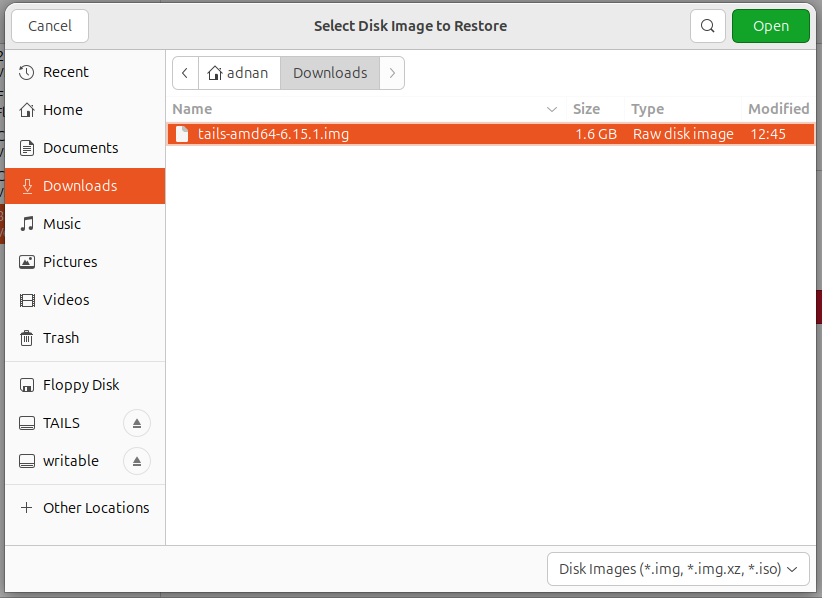
Confirm to start writing Tails on USB:
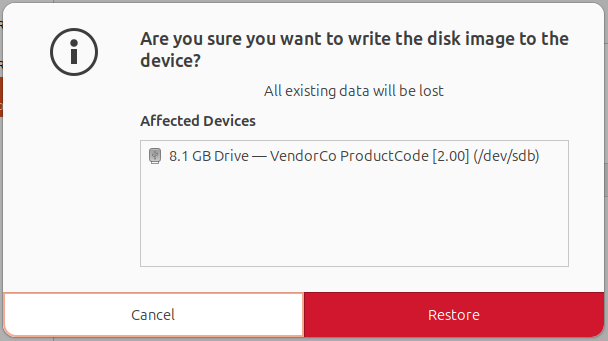
This will take a few minutes. Once all done, you can eject the drive and boot from the USB to run Tails in an isolated environment.
- Installation Option 2: Installing Tails Using the balenaEtcher
First, you must download and install the Balena Etcher on your respective Linux distribution.
Once installed, you have to make the USB bootable with the Tails disk image that you have already downloaded.
Follow this guide to briefly understand how to install and use Balena Etcher
Setting Up Persistent Storage and Administrator Password
When you boot from Tails, you will have to pass through the following interface, where you can create persistent storage and set the administrator password.
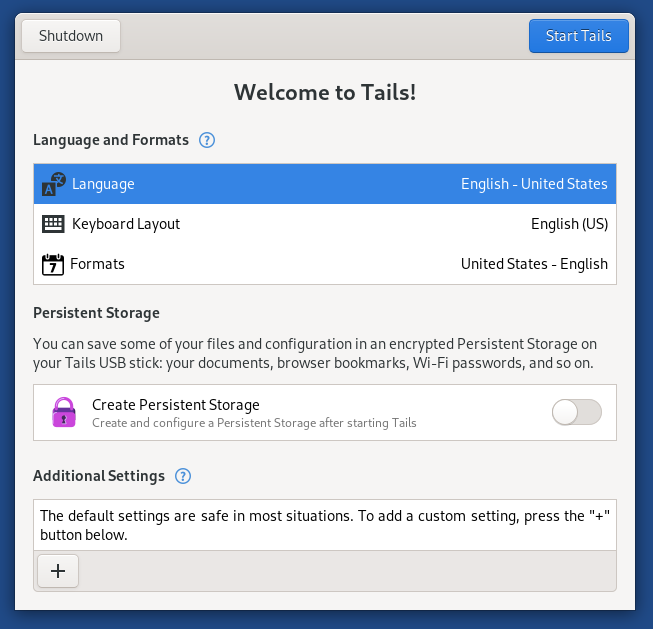
- Persistent Storage: To keep the data, history for further sessions.
- Administrator Password: To handle the permissions or admin password required for installing applications.
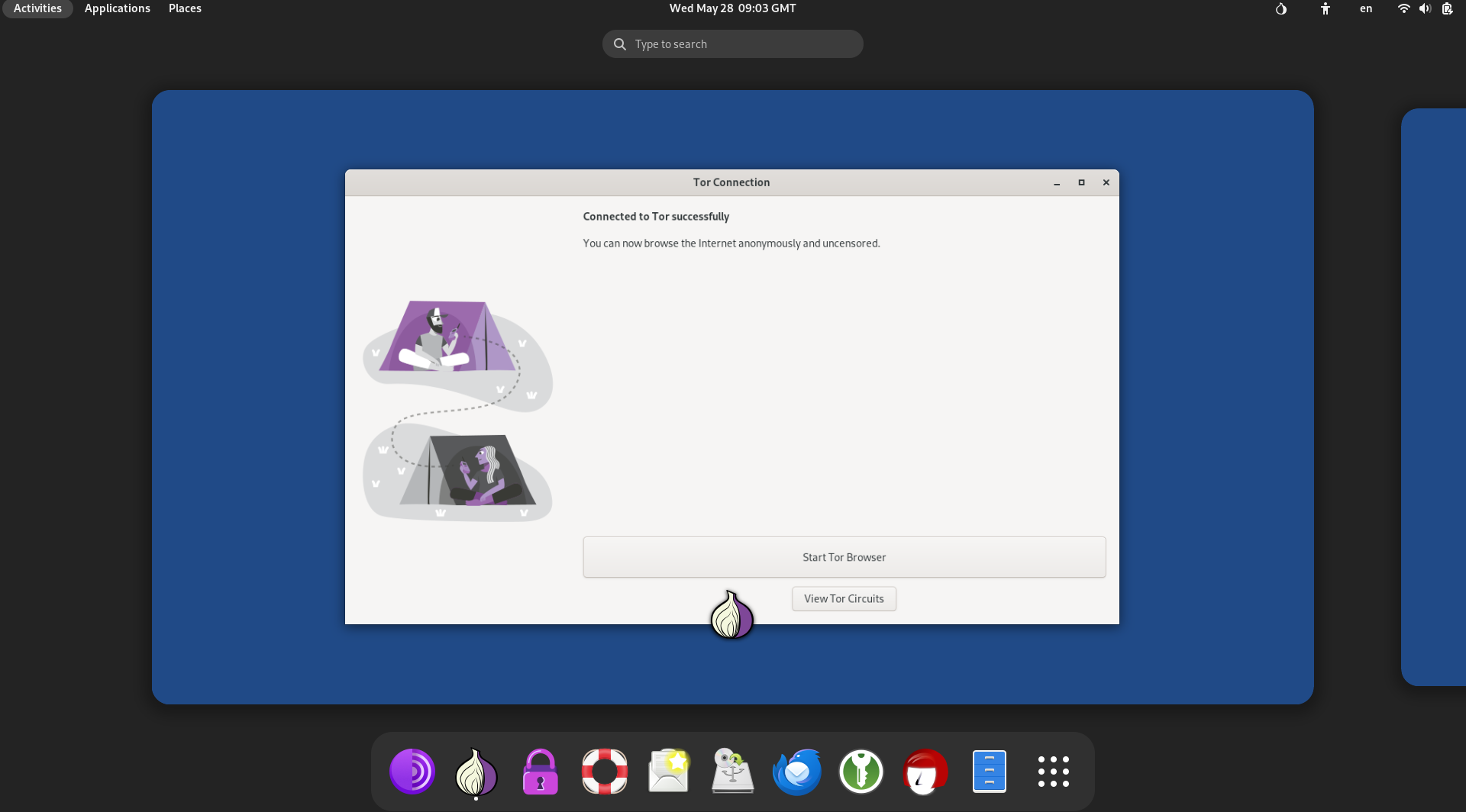
Now, you have to set the Tor connection, where you have two options, i.e., choose “Connect to Tor automatically”.
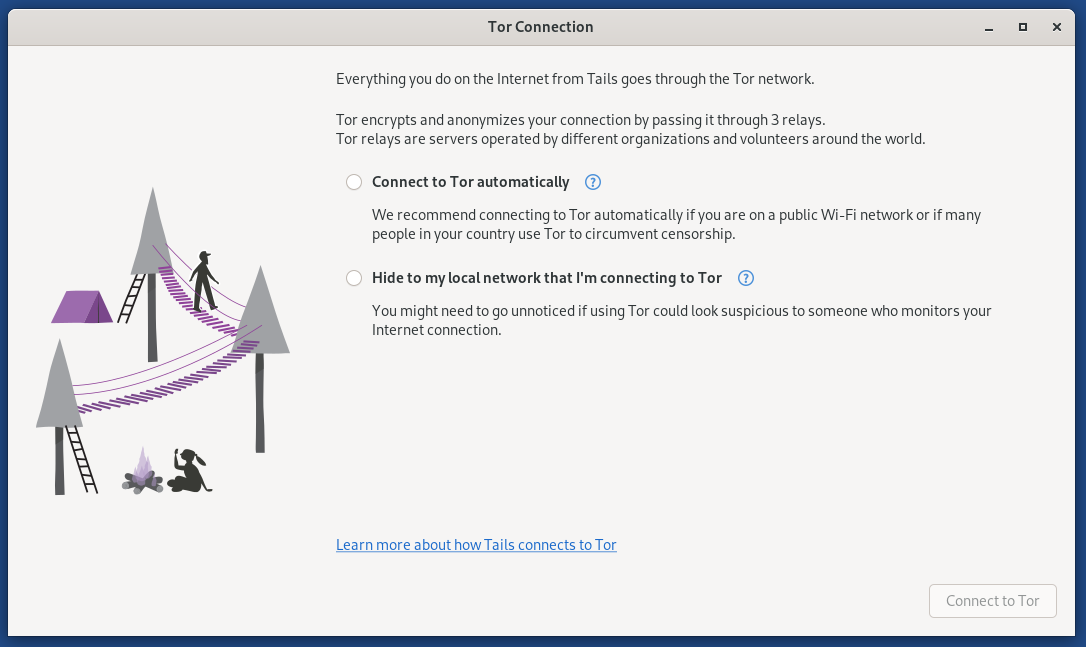
This way, you can set anonymity through Tails.
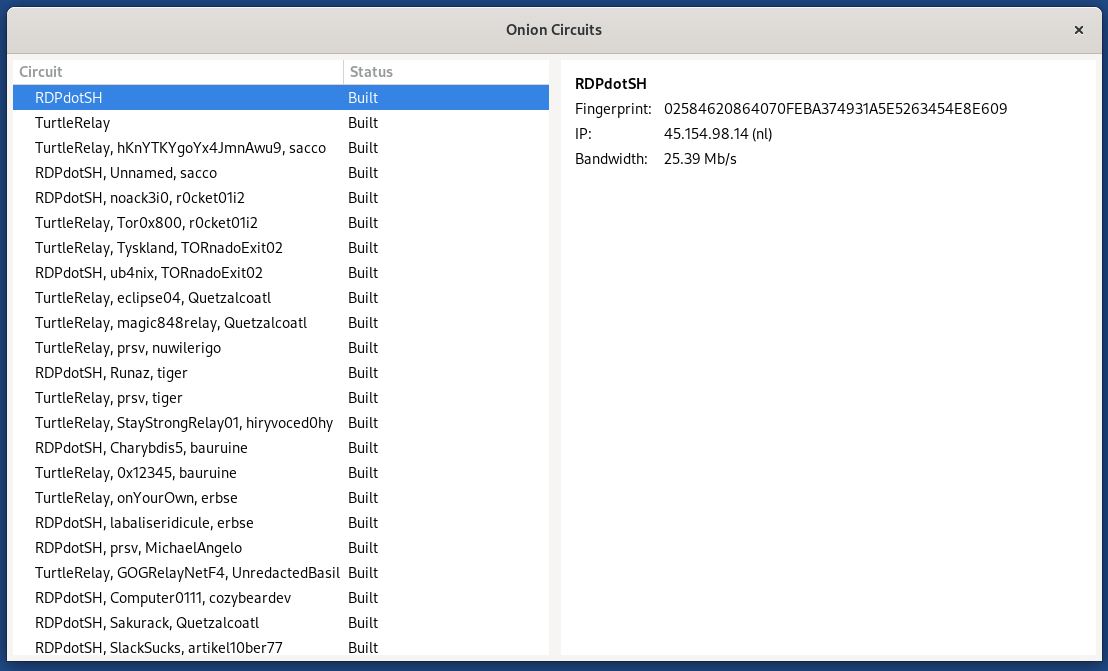
- What is Tor/Onion Circuits: The Path that the Tor network uses to route traffic from a user’s device to the destination server with anonymity.
Here’s the terminal look of the Tails:
Here you go with the Tails:
Should You Use Tails? | Technical Pros and Cons
If you still have questions about whether Tails is a perfect fit for me or not, don’t worry, I have compiled a technical Pros/Cons of Tails to assist you in this regard:
| Technical Feature/Component | Pros | Cons |
|---|---|---|
| Tor-based Anonymity | Routes traffic through the Tor network by default. | Some websites discourage the Tor Project. |
| Data Security | It’s RAM-dependent, and thus, data is wiped out after every boot, i.e., no data breach or tracing through data | Data is lost, i.e., the new Tails user who is not familiar with non-persistent working. Once the user is familiar with the system, this issue will decrease. |
| Privacy Tools | Built-in tools for file sharing, password, email client, etc. | Limited application availability (outside the default installation) |
| No Installation | Just plug and play. Plug in the live USB of Tails, and you are good to go. No hard and time-consuming installations. | Unstable performance compared to the full-fledged installed system. |
| Hardware Protection | Tails spoofs MAC addresses. So, nothing beyond that when it comes to security. | It may malfunction sometimes, i.e., in a conflict with the internet hardware devices. |
| Disk Image Verification | Disk Image is briefly verified on the Tails official website. | It might be difficult for the new or non-technical users. |
| System Footprint | A very small footprint, i.e., negligible, because of the advanced encryption/protection level. | This makes it not suitable for routine or daily tasks. |
| Updates | Frequent Updates,i.e., every 6 weeks. | Create a bootable system with every update. |
Pro-Tip: For maximum security, always use the non-persistent USB for Tails and enjoy this state-of-the-art tool in the tech era.
Conclusion
Tails OS is one of the best anonymity tools based on the Debian distro and is a part of the Tor project. With one end in Open Source (Linux-based) and the other in anonymity (Tor project).
Tails OS is installed and used as a Live non-persistent USB, which minimizes the risk of any traces. Today, I have drafted an in-depth review of the Tails OS, including its installation on a USB as well.
FAQs:
Q1: Is Tails OS Legal?
Yes, Tails is legal. Tails is an open-source Debian-inspired Tor project. The Onion Routing (Tor) nature of Tails makes it suspicious but not illegal.
Q2: Does Tails hide your IP?
Tails is a Tor project, and when routing, it hides your IP and server information.
Q3: Does Tails run in RAM?
Since it’s an amnestic, no data or history is kept. This anonymity is due to RAM. It temporarily stores data and refreshes it after each session.
Q4: What is the Tails filesystem?
Tails works on the Ext4 file system, i.e., Fourth Extended Filesystem.
Recommended Comments