From OpenBSD to Linux: How Pledge can Enhance Linux Security
Sat, 08 Mar 2025 08:54:21 GMT

Imagine a scenario, you downloaded a new binary called ls from the internet. The application could be malicious by intention. Binary files are difficult to trust and run over the system. It could lead to a system hijacking attack, sending your sensitive files and clipboard information to the malicious server or interfere with the existing process of your machine.
Won’t it be great if you’ve the tool to run and test the application within the defined security parameter. Like, we all know, ls command list the files in the current working directory. So, why would it require a network connection to operate? Does it make sense?
That’s where the tool, Pledge, comes in. Pledge restricts the system calls a program can make. Pledge is natively supported on OpenBSD systems. Although it isn’t officially supported on Linux systems, I’ll show you a cool hack to utilize pledge on your Linux systems.
What makes this port possible?
Thanks to the remarkable work done by Justine Tunney. She is the core developer behind the project- Cosmopolitan Libc.
Cosmopolitan makes it a bridge for compiling a c programs for 7 different platforms (Linux + Mac + Windows + FreeBSD + OpenBSD 7.3 + NetBSD + BIOS) at one go.
Utilizing Libc Cosmopolitan, she was able to port OpenBSD Pledge to the Linux system. Here's the nice blog done by her.
Restrict system calls() with Pledge
You might be surprised to know one single binary can run on 7 different platforms - Windows, Linux, Mac, FreeBSD, OpenBSD, NetBSD and BIOS.
These binary files are called Actually Portable Executable (APE). You can check out this blog for more information. These binary files have the .com suffix and it’s necessary to work.
This guide will show how to use pledge.com binary on your Linux system to restrict system calls while launching any binaries or applications.
Step 1: Download pledge.com
You can download pledge-1.8.com from the url- http://justine.lol/pledge/pledge-1.8.com.
You can rename the file pledge-1.8.com to pledge.com.
Step 2: Make it executable
Run this command to make it executable.
chmod +x ./pledge.comStep 3: Add pledge.com to the path
A quick way to accomplish this is to move the binary in standard /usr/local/bin/ location.
sudo mv ./pledge.com /usr/local/binStep 4: Run and test
pledge.com curl http://itsfoss.comI didn’t assign any permission (called promises) to it so it would fail as expected. But it gives us a hint on what system calls are required by the binary ‘curl’ when it is run.
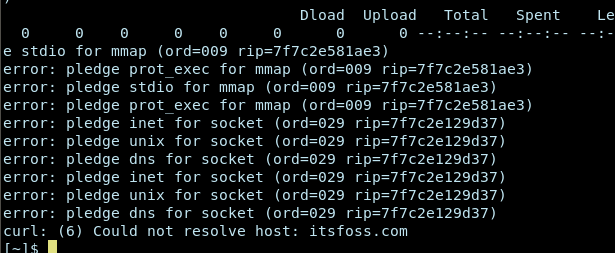
With this information, you can see if a program is requesting a system call that it should not. For example, a file explorer program asking for dns. Is it normal?
Curl is a tool that deals with URLs and indeed requires those system calls.
Let's assign promises using the -p flag. I'll explain what each of these promises does in the next section.
pledge.com -p 'stdio rpath inet dns tty sendfd recvfd' \
curl -s http://itsfoss.com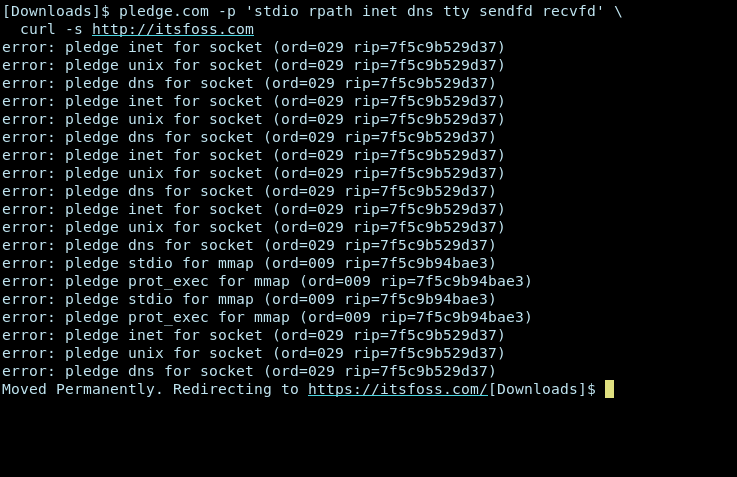
It’s successfully redirecting to the https version of our website. Let’s try to see, if with the same set of promises, it can talk to https enabled websites or not.
pledge.com -p 'stdio rpath inet dns tty sendfd recvfd' \
curl -s https://itsfoss.com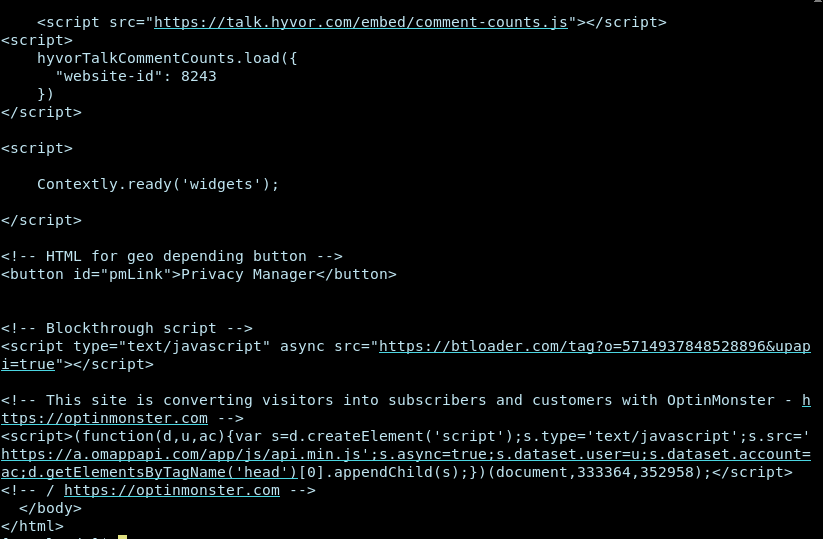
Yeah! It worked.
A quick glance at promises
In the above section, we used 7 promises to make our curl request successful. Here’s a quick glimpse into what each promises intended for:
- stdio: Allows reading and writing to standard input/output (like printing to the console).
- rpath: Allows reading files from the filesystem.
- inet: Allows network-related operations (for example, connecting to a server).
- dns: Allows resolving DNS queries.
- tty: Allows access to the terminal.
- sendfd: Allow sending file descriptors.
- recvfd: Allow received file descriptors
To know what other promises are supported by the pledge binary, head over to this blog.
Conclusion
OpenBSD’s pledge follows the Least Privilege model. It prevents programs from mis-utilizing system resources. Following this security model, the damage done by a malicious application can be quite limited. Although Linux has seccomp and apparmor in its security arsenal, I find pledge more intuitive and easy to use.
With Actually Portable Executable (APE), Linux users can now enjoy the simplicity of pledge to make their systems more secure. Users can provide more granular control over what processes can do within these environments would add an extra layer of defense.
Author Info

Bhuwan Mishra is a Fullstack developer, with Python and Go as his tools of choice. He takes pride in building and securing web applications, APIs, and CI/CD pipelines, as well as tuning servers for optimal performance. He also has passion for working with Kubernetes.

Recommended Comments